Creating Policies
We will enact fine-grained control on both the source and destination buckets by giving only the required permissions to the read user, the write user (both used by the TitanQ solver) and the supervisor user (used by you to prepare requests and retrieve results).
This is accomplished by writing policies that will link an S3 resource to one or more permissions. Later on, we will attach these policies to users.
| Policy | Permission(s) | S3 Resource | Used by |
|---|---|---|---|
| read policy on source bucket | read (s3:GetObject) | source bucket | The TitanQ solver read user |
| write policy on destination bucket | write (s3:PutObject) | destination bucket | The TitanQ solver write user |
| write policy on source bucket | write (s3:PutObject) | source bucket | Customer's supervisor user |
| read policy on destination bucket | read (s3:GetObject) | destination bucket | Customer's supervisor user |
Read-Only Policy for source bucket
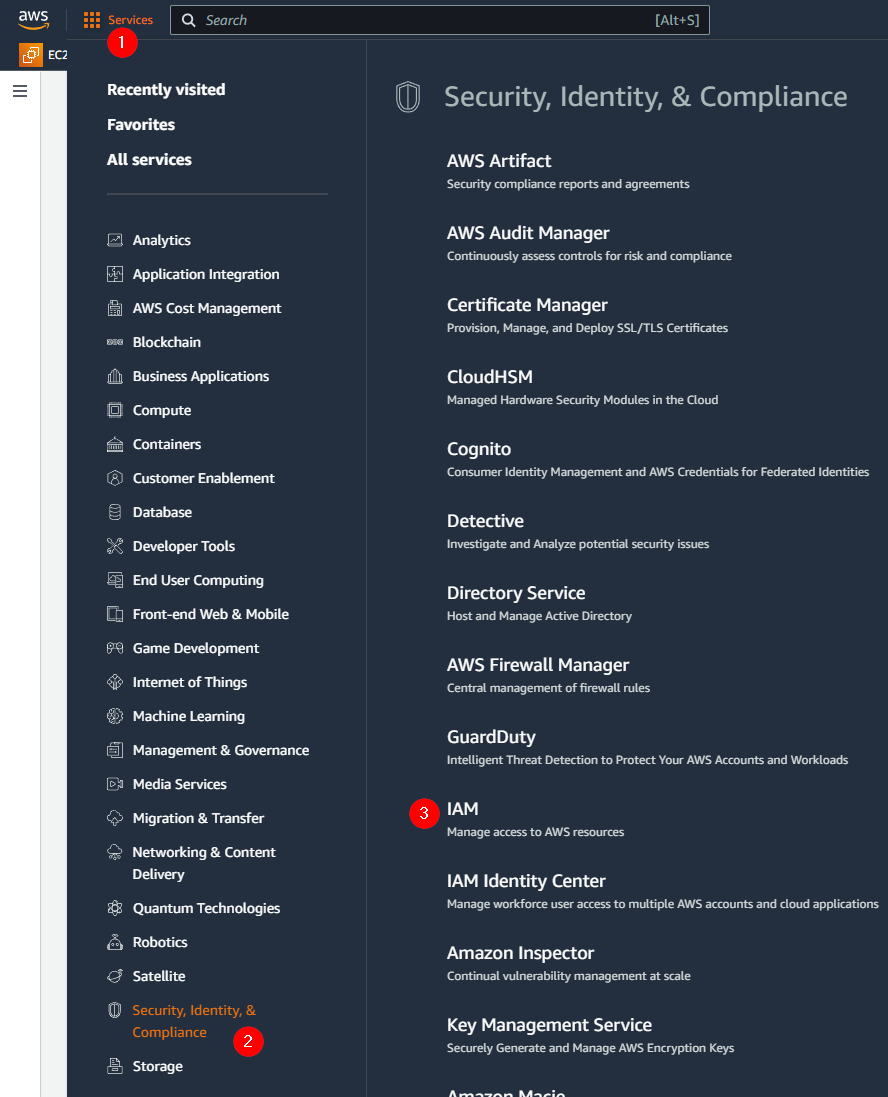
Go to the IAM dashboard (not the IAM Identity Center):
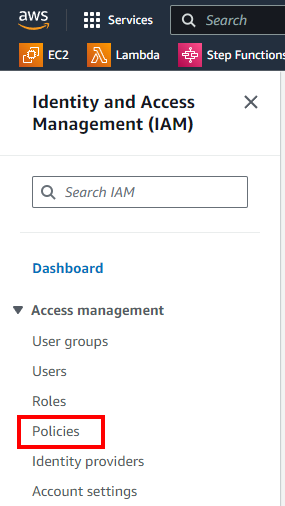
Select the Policies submenu:
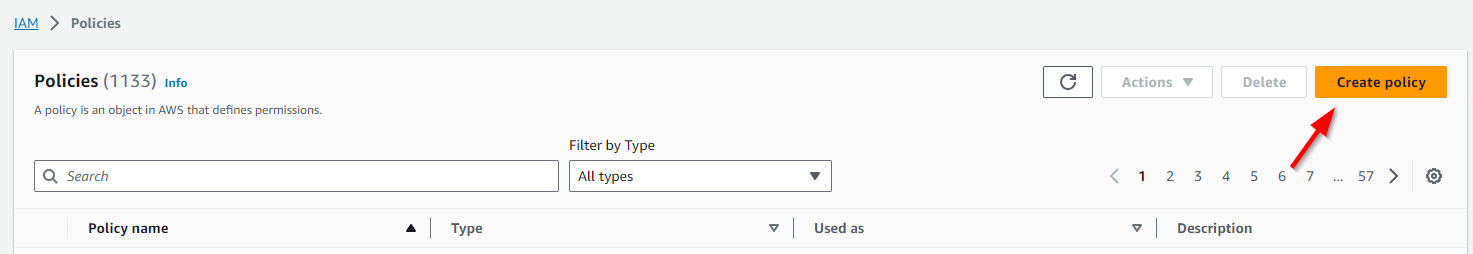
Select Create Policy:
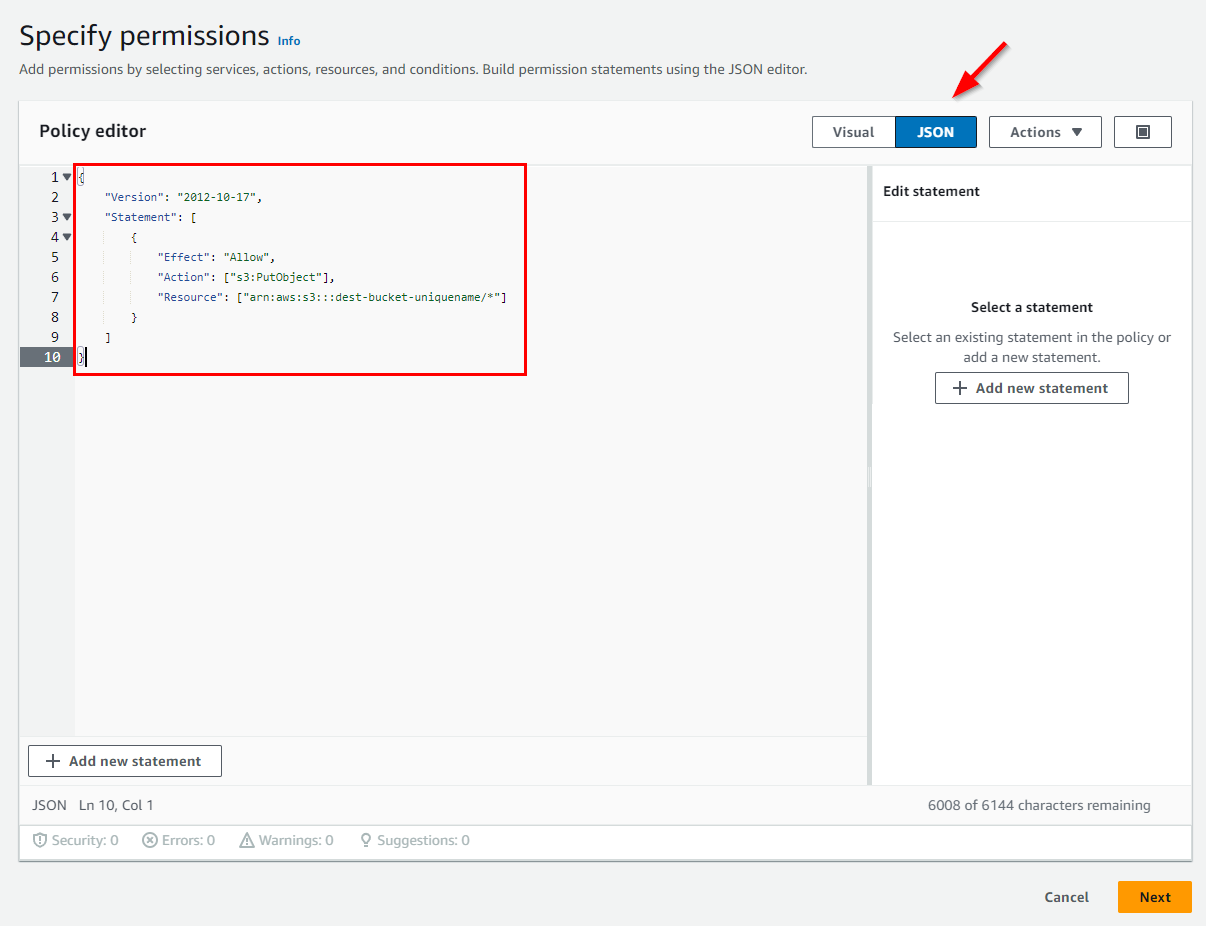
Select the JSON edit mode and paste the following in the editor area:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["s3:GetObject"],
"Resource": ["arn:aws:s3:::source-bucket-uniquename/*"]
}
]
}
where the Resource key should be adjusted to match your own source bucket ARN from the previous step.
Click Next
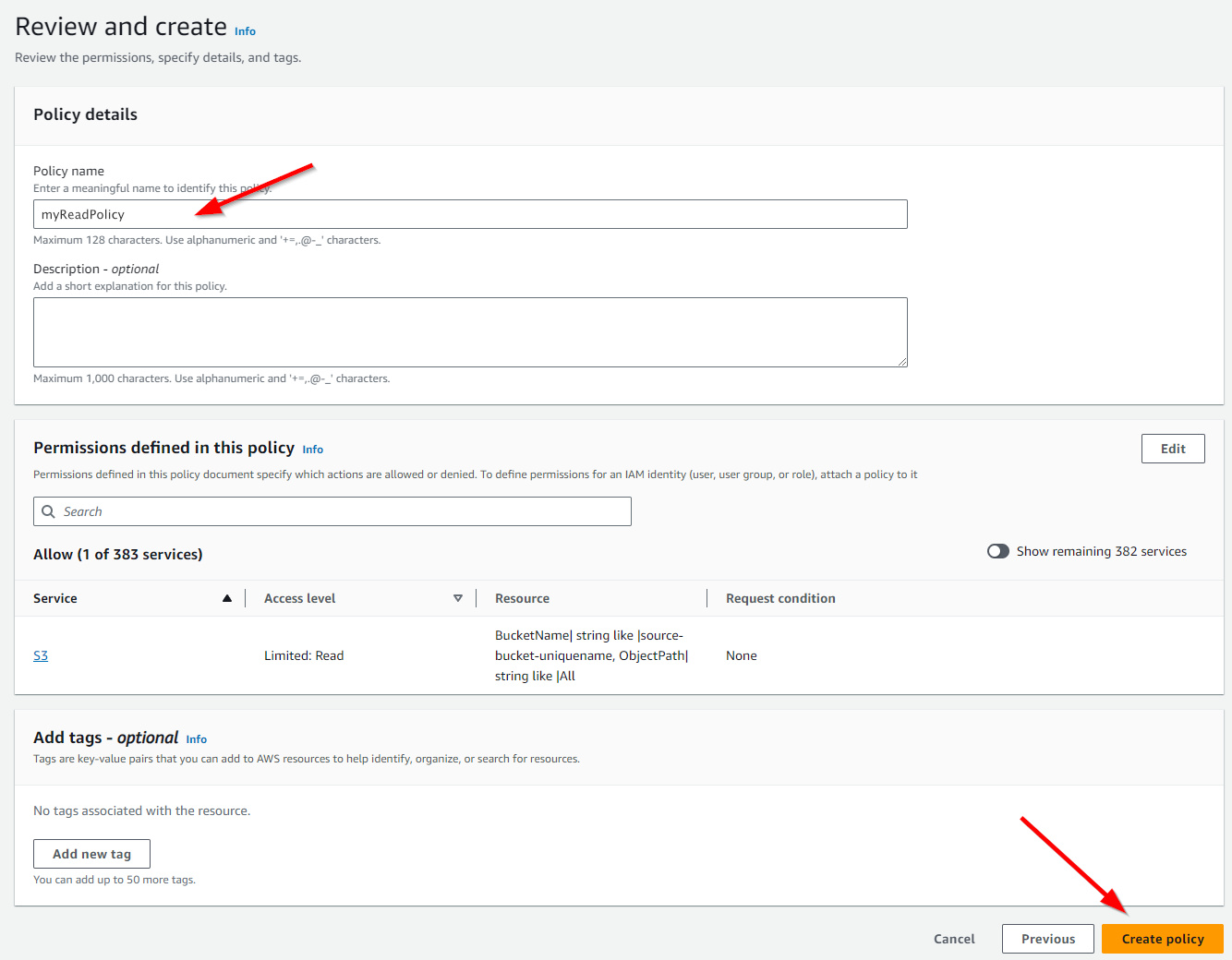
In the following "Review and Create Policy" dialog, enter a policy name, eg. myReadPolicy and click Create.
Write policy for the destination bucket
Do the same for the destination bucket, this time using the following JSON Policy description instead:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["s3:PutObject"],
"Resource": ["arn:aws:s3:::dest-bucket-uniquename/*"]
}
]
}
Policies for the supervisor user
Once again, create two new policies:
- write access to the source bucket called eg.
supervisorWritePolicy - read access to the destination bucket called eg.
supervisorReadPolicy
- supervisorWritePolicy
- supervisorReadPolicy
write permission to the source bucket:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["s3:PutObject"],
"Resource": ["arn:aws:s3:::source-bucket-uniquename/*"]
}
]
}
read permission to the destination bucket:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["s3:GetObject"],
"Resource": ["arn:aws:s3:::dest-bucket-uniquename/*"]
}
]
}